My previous blog discussed how the path to greater cybersecurity maturity requires viewing security as more than just mandatory to running the business, but also as a key enabler of change and growth.
This blog continues our cybersecurity insights from the CGI Global 1000 outlook, drawn from in-person conversations with 1,000 senior business and technology leaders. It offers suggestions to help leaders reduce the cost of running cybersecurity so they can invest in their enterprises’ digital transformation, and advance their own cybersecurity staff to perform higher value processes.
Shifting the cybersecurity focus from a day-to-day reactive mode to forward-thinking enablement requires enterprises to understand two things:
- How cybersecurity is a function of running their organization, and
- Where their internal cybersecurity resources bring the most value across the run, change and grow dimensions
For every $1 million spent on cybersecurity, an estimated $950,000 is spent just to run the operations. Because of this imbalance, many enterprises operate in fire-brigade mode, reacting to external alerts of bugs, malware or bad actors. To help organizations move to a proactive approach, they must first find practical ways to reduce cybersecurity costs and increase capabilities in the face of cyber talent shortages.
6 areas for liberating cybersecurity resources
Outsourcing basic cybersecurity functions to trusted partners helps enterprises reduce costs and improve their security postures, while also freeing staff and budget for change-focused initiatives. It does require, however, that desired security outcomes be identified to determine how best to source the capabilities needed to deliver those outcomes. Just as most organizations don’t need their own in-house database administrators, they also don’t need—and would be challenged to maintain—their own cyber forensics experts or advanced technology experts.
Following are six key areas where outsourcing cybersecurity can help:
-
Asset optimization

Rather than buying the next cool technology, enterprises should first focus on how to optimize their current security assets. A trusted expert can assess what can and should be done with existing assets to improve the security posture, and provide the expertise to optimize the technology itself.
-
Holistic view
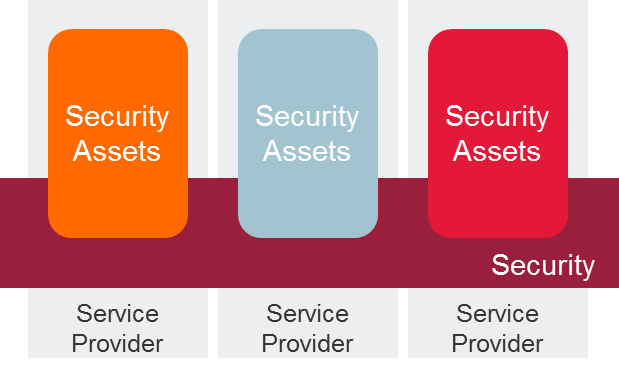 Often, cybersecurity assets are scattered throughout an organization and/or are from myriad vendors. Different teams are responsible for end-user services, corporate/virtual private networks, security, etc. For example, firewalls typically are purchased and managed by network teams and not under the direct supervision of cybersecurity teams. This complexity creates inefficiencies and exposes new threats. A holistic view can reduce the risks related to threat vectors from different assets. As an example, combining server assets, endpoint security and perimeter security can create a stronger security posture against ransomware.
Often, cybersecurity assets are scattered throughout an organization and/or are from myriad vendors. Different teams are responsible for end-user services, corporate/virtual private networks, security, etc. For example, firewalls typically are purchased and managed by network teams and not under the direct supervision of cybersecurity teams. This complexity creates inefficiencies and exposes new threats. A holistic view can reduce the risks related to threat vectors from different assets. As an example, combining server assets, endpoint security and perimeter security can create a stronger security posture against ransomware. -
Monitoring and analysis
Enterprise cybersecurity resources often are tied down by the day-to-day management of security monitoring and analysis. When done properly, this work requires 24/7 cybersecurity staff that can be difficult to attain. This function should be one of the first domains to outsource to third-party experts.
-
Forensics
It is often too difficult for most enterprises to build and maintain their own forensics teams. These experts are scarce, expensive and demand challenging and exciting work. (See my colleague Andrew Rogoyski’s blog, A pragmatic solution to the cyber talent shortage: Co-sourcing.) Providers of managed security services have the deep bench of high-end specialists that is needed, and interact with industry consortia to provide superior services at a shared services price.
-
Security technologies
With so many security technologies out there (e.g., next-generation firewalls, web application firewalls, intrusion detection/prevention systems, security information and event management software, etc.), it is challenging to maintain, run and maximize these without deep expertise. While more mature enterprises may keep up with day-to-day security operations, most do not maximize their advanced tools because they lack the deep know how to do so. It takes a really large security organization to have enough trained experts to get the most out of these tools. The good news is, third-party service providers have this covered and know how to block ever more threat vectors with existing tools.
-
Less-secure legacy environments
Just as they have outsourced Windows 2003 server farms, enterprises can outsource legacy systems that have security “holes” to a provider that is expert in addressing security in such situations. Another option is to modernize the technology through Software as a Service that offers superior security features.
These outsourcing changes follow the same path taken by traditional IT years ago, as stated in my previous blog. Security is not an exception to this pattern. Security leaders need to stay current and liberate the running of cybersecurity to enable the digital transformation of the enterprise. This move to outsourcing can be achieved in a phased approach with prescribed tracks, or as a single transformational outsourcing effort. My next blog post will discuss cybersecurity’s role in enabling change.