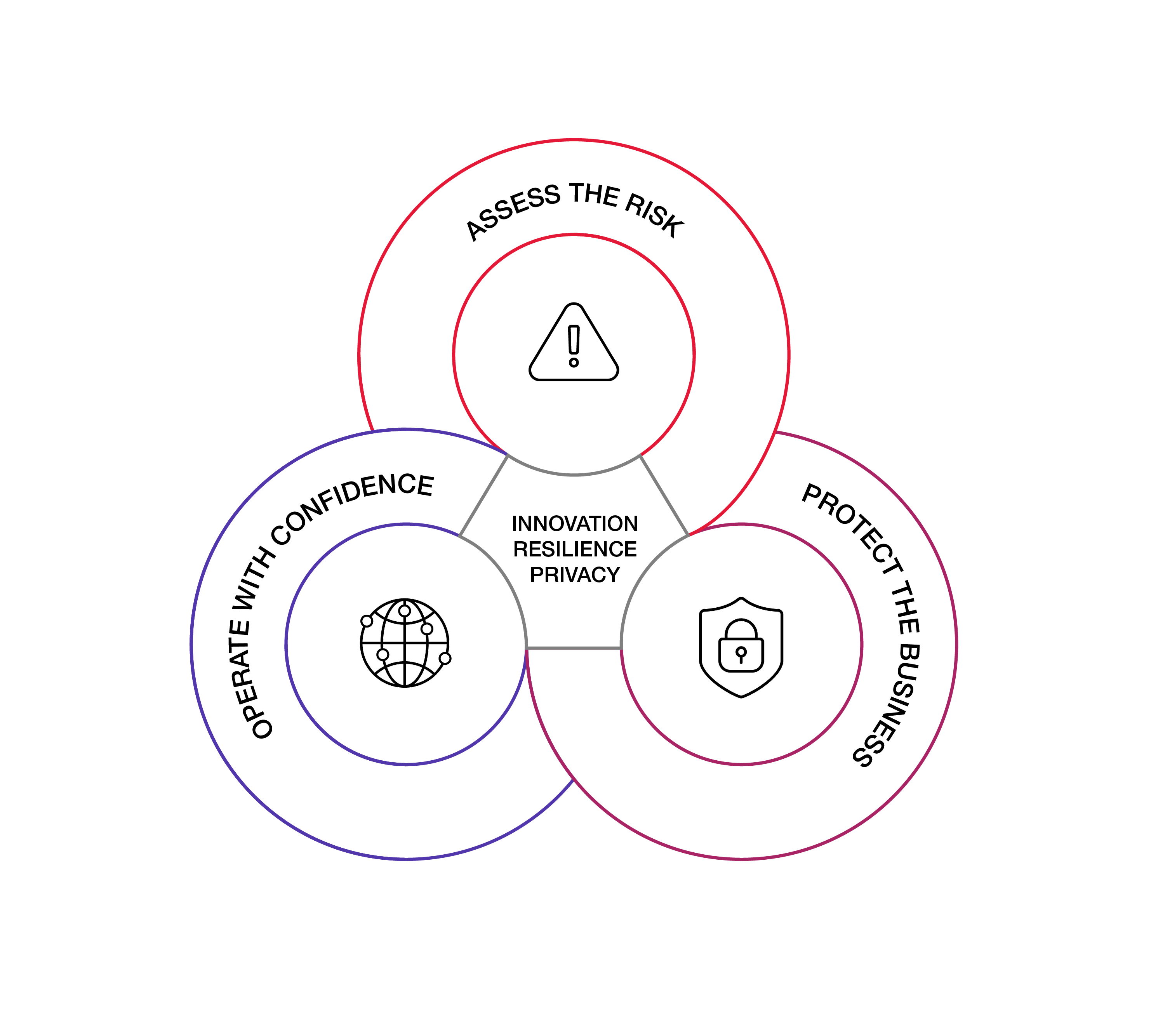
Hervé est le leader mondial du service-conseil en cybersécurité et en gestion des risques de CGI. Il dirige également les activités conseil sécurité, risque et continuité d’activité chez CGI Business Consulting en France.
Blogue