Cyber attacks are becoming increasingly sophisticated, targeting people, networks and devices. Attackers are finding new ways into organisations by-passing the perimeter security walls and stealing valuable information or disrupting business. Organisations need to be agile, adopt new technologies, operate with customers and suppliers across the world and be confident that they are secure.
Our Advanced Cyber Threat Investigation Service
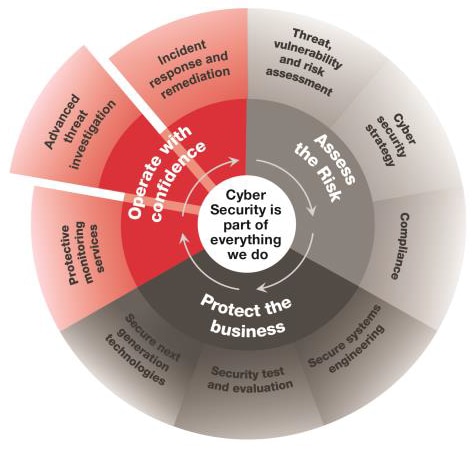
Our Advanced Threat Investigation service is provided from our Cyber Centre by our highly skilled and experienced cyber security analysts. They review the latest cyber threat information from multiple sources. Using automated tools and expert analysis, they detect, investigate and respond to sophisticated advanced threats to protect an organisation.
As a leading supplier of cyber security services in the UK, Europe and North America, we offer the full range of services to secure your organisation. Our Advanced Threat Investigation (ATI) service provides specialist threat based analytics services to augment traditional Protective Monitoring activities such as those provided by our ten Security Operations Centres (SOCs).
We provide a comprehensive set of analytic capabilities that can be scaled to the type of organisation and the threats faced. Our ATI service draws on multiple information sources, tools and security systems to provide a combination of automated analysis and expert insight to detect and respond to advanced network threats.
Through our Protective Monitoring service we work closely with security organisations to help defend against intrusion attempts against our client’s networks. The ATI service goes a step further and provides investigative capabilities before and after an attack has occurred.
Our ATI service is provided as an extension of our Protective Monitoring service. We can set up the service within a few weeks, without disruption to existing activity. We can find the advanced attacks that get past standard protection methods. So, you can be confident that your organisation is protected from cyber attack.




